BYOD is a fact of life in workplace environments.
When properly implemented, BYOD can cut hardware and services costs. It allows employees to use the devices that they are most familiar with and saves companies in training and related expenses.
But an improperly implemented BYOD program can be a nightmare.
Here’s what happened at Sesame Workshop, the makers of the children’s show Sesame Street:
A few years ago, Noah Broadwater, CTO of Sesame Workshop, noticed an alarming tendency in his organization. Employees at the New York City-based educational media company…were buying almost any device they liked for use in the workplace and having the cost of it signed off on expenses by their departmental managers.
This situation was clearly untenable. None of these devices were inventoried and the company was losing money supporting these devices.
Sesame Workshop solved the issue by asking employees to select a device from a pre-approved list which the company would buy at a reduced rate.
BYOD concerns in the enterprise
But excessive support costs are not the only factor that CIOs have to deal with when implementing BYOD. There are other issues, like:
1) Data security
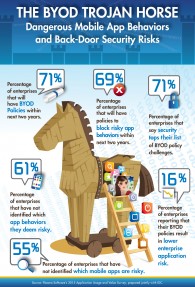
Securing data in an enterprise network in a BYOD environment is a major challenge. According to a report by Flexera Software and IDC 71% of enterprises consider security to be their biggest BYOD issue.
Image source
Beyond security issues and costs, there are also other teething troubles that CIOs will have to grapple with when giving the green light to BYOD.
2) Employee privacy
Employee privacy is a big deal. Many companies adopt practices like remote data deletion in the event of a device being lost or stolen.
However, because employee data is also stored on these devices there is a danger that this data can also be wiped out, leaving companies liable to lawsuits.
3) BYOD incompatible networks
Network availability also becomes a major challenge in a mobile first workplace. Companies will have to invest more in Wireless LAN to handle the influx of employee devices in the workplace.
4) Device authentication
Unlike in a traditional enterprise network where devices were locked down, no device can be completely trusted in BYOD workplace. There is a need to strike a fine balance between not inconveniencing users by making them repeatedly authenticate the device on the network and ensuring that rogue devices don’t connect. Creating a device profile and monitoring device behavior for unknown patterns is one solution.
Creating a common sense BYOD policy
BYOD’s success depends on the cooperation of employees. This is why CIOs must lead in creating a BYOD policy that is easily understood, clear, and concise. This policy must balance the needs of both the employers and the employees.
Take cognizance of these elements when you are writing a policy for your company:
1) Permitted and prohibited services and devices
Make a list of all the acceptable devices and services that employees are permitted to use in the corporate network. Depending on the device not all services might be made available- for example, on some devices only email might be supported, while on others full-range of apps can be allowed or supported.
2) Rules governing storage of company data on private devices
Clearly specify the protocols associated with company data stored on employee devices. Can data be deleted by employees? Who is responsible for backing up the data, and what’s the schedule of backup, if any?
3) Employee privacy expectations
The policy must also clearly inform the employees how corporate data would be stored, and to what extent IT will have access to the employee device in order to monitor compliance with policies. It should specify that companies are not responsible for loss of employee data.
4) Rules governing lost or stolen devices
The standard procedure when a device is lost or stolen is remote data wipe. The policy must specify the steps an employee should follow when they discover that their device is lost or stolen. Employees participating in the BYOD program must consent to remote wipes.
5) Rules governing costs
The policy must also specify the company’s obligations regarding data costs for out of office work. Not clearing this up can result in confusion and excessive expense claims.
6) Compliance with regulations
For companies in highly regulated industries like finance and healthcare the policies must be designed to comply with laws like HIPAA. For example, there should be clear-cut policies in the healthcare sector about what kind of information is permitted to be stored or accessed by mobile devices.
7) Post-termination protocol
The policy must also specify the protocol that would kick in when the employee is no longer with the organization. This section should deal with device de-authentication, data scrubbing and other data sanitization processes that IT will follow to ensure that sensitive data does not remain on the device and it can no longer connect to the enterprise network.
Employee training as key
After you draft the policy consult the actual users, and modify where necessary. You should also ensure that employees are trained in compliance so that they don’t inadvertently cause a data breach by not following best practices.









Sweet site, super design and style, real clean and utilize pleasant.
https://www.smortergiremal.com/